The recent WannaCry ransomware made global headlines infecting and alerting everyone from government, healthcare, communication providers, automotive companies to corporations and the general public of their vulnerabilities.
Cyberattacks come from different angles and in many forms looking for that right way into your computer and network. They look to take advantage, spread, collect sensitive information, corrupt files, lock down for ransom and even destroy systems or networks. You’re vulnerable from both sides of the firewall; cyber and the human element.
What is Malware, Virus and Ransomware?

First, malware is a broad term covering a range of malicious code to other items you might have heard of, such as spyware, adware, nagware, trojans, worms and yes, viruses. A virus is also a broad term which can be a specific malware in that it infects systems and can spread throughout networks replicating itself.
A virus is typically designed to infect, copy itself, corrupt system files, delete files and either damage or destroy your computer. Whereas a malware (as can do the same) can infect, hide and use your computer to steal your information, use you to spread across your home or company network, email system and replicate its process.
- This means one (1) person could potentially share it amongst the whole home, company network and everyone in their contact list. This results in the creator receiving all the important family or corporate information they desire, encrypting all your files and potentially charging you a fee to get your computer and or sensitive data back.
WannaCry Malware / Ransomware?
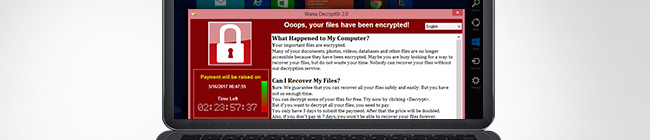
This type of malware infects your computer system; the ransomware encrypts all the files on your computer restricting you from any access to them. Remaining is a very unpleasant screen informing you your information / computer is being held ransom forcing you to pay a fee to release your data and have access back to your computer and your data.
Cybersecurity experts see the first round of WannaCry 2.0 cyber-attack slowing down, but there’s a high chance other variants making their way back.
What did we learn from WannaCry ransomware?
Don't overlook the small things. The WannaCry ransomware attack recently impacted cyber security on computers around the world that didn't run their system updates, didn’t have backups and didn’t have any anti-malware protection.
How does it get on my computer system?
Luckily, ransomware doesn’t just magically appear on your computer. Unfortunately, there are a few tricky ways in which malware can install itself on your computer; either directly or indirectly.
- It has to be downloaded.
- And as smart as we are, there are tricky ways for malware to automatically download itself onto your computer.
- Unsecured USB drives can easily help store and transport viruses, malware / ransomware.
- USB drives are found, given out at events or shared amongst friends or co-workers. A lot of people use an unsecure USB drive containing home files and company (work) information – at work this is also known as “Bring Your Own Device” (BYOD).
- Someone may unknowingly have an infected computer and data being transferred to an unsecured USB drive may contain the variants. Thus, downloading and installing itself when plugged into a work computer or any other system it gets plugged into.
- It’s more than emails - An attack known as a drive-by can get you if you simply visit certain websites.
- Cybercriminals are able to hide and embed their malware into ads or links on websites. Our quest for information when searching online sometimes leads us to new unknown sites. Sometimes, when you click links that take you to such sites or while you visit such sites, you can unknowingly download the malware / ransomware.
- Cybercriminals love to target their ransomware messages to special times of year.
- Holiday shopping seasons and birthdays - You might get emails or ads promoting your favorite places to eat, shop, relax or have fun. In most cases, these look legitimate making your decision to click links, download coupons and print items that much easier without thought.
What preventive measures can I take?

Here are a few simple steps you can take to protect yourself.
- Computer system updates
- Making sure you keep your computer’s operating system up-to-date when system updates are available; this helps protect from vulnerabilities and potential cyberattacks.
- Having an Anti-Virus / Anti-Malware software protection solution on your computer system.
- Have a company policy / standard of best practices to include frequent computer and network updates.
- Include an Encrypted USB as a part of standard issue with laptops and company badges along with ongoing training / orientation with respect to current events and regulations.
- See our “Using and promoting encrypted USB Flash drives in your organization” for insight into setting up and applying company policies / standards.
- Be sure to be up-to-date with domestic and international regulations; EU GDPR and NYDFS
- Always remember to back up and protect your files.
- Back up files to a cloud service like Amazon Cloud, Google Drive or Apple’s iCloud.
- Back up files to a secure encrypted USB Drive / external drive.
Note: Hardware-encrypted USB drives with Anti-virus / Anti-malware make the most secure standard in protecting your data both as storage backups and in protecting your data while in transit; when using it for business / work, traveling, events and home applications.
Kingston Encrypted USB with Anti-Virus / Anti-Malware for secure data protection
Kingston keeps you compliant, prepared with the latest technology and sets the highest standard in data security.
- 256-bit AES hardware-based encryption, in XTS mode with FIPS
- *Advanced Anti-Virus / Anti-Malware and Management protection solutions
- Simple, easy to use solutions designed for quick and easy deployment
- Essential for personal data protection to corporate and government / military applications

Learn more about Kingston Encrypted USBs and protecting your data
Learn More about, Encrypted USB Drive - Kingston Technology
*Available option with additional fee (see product pages for more information)





