AES-XTS Block Cipher Mode is used in Kingston IronKey Hardware-Encrypted USB and External SSD Drives
XTS - The Key to the Best Encryption
It takes more than a certificate to have the most secure USB drive encryption. Kingston IronKey™ hardware-encrypted USB and external SSD drives feature 256-bit AES encryption utilizing XTS block cipher mode. XTS provides greater data protection over other block cipher modes, such as CBC and ECB.
The following details the security advantages of the IronKey drives, which are engineered from the ground up as data protection devices.
Full-Disk Encryption AES Block-Cipher Modes of Operation
AES, or Advanced Encryption Standard, is a block cipher that encrypts blocks of data in 128 bits. To encrypt anything larger than 128 bits, AES uses a block cipher mode. There are many different AES block cipher modes that are part of the AES specification. The simplest block cipher mode is Electronic Code Book (ECB). Cipher Block Chaining (CBC) addresses security weaknesses with ECB and is one of the most common modes used in portable encrypting Flash drives. XTS is one of the newest modes and provides stronger data protection over ECB and CBC. The following is a brief description of these block cipher modes.
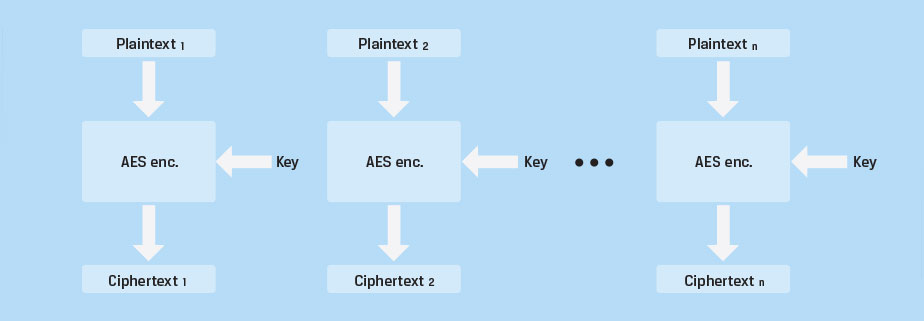
Electronic Code Book (ECB). This cipher mode simply repeats the AES encryption process for each 128-bit block of data. Figure 1 depicts data encryption using ECB mode. Each block is independently encrypted using AES with the same encryption key. For decryption, the process is reversed. With ECB, identical blocks of unencrypted data, referred to as plain text, are encrypted the same way and will yield identical blocks of encrypted data (cipher text). This cipher mode is not ideal since it does not hide data patterns well. Figure 2 is an example that demonstrates the major security vulnerability with this cipher mode.
 |
|
Electronic Code Book (ECB) |
The unencrypted image is shown on the left. The image on the right shows what the cipher text might look like when using other encryption modes such as CBC or XTS. The center image clearly demonstrates the vulnerability associated with ECB. Since identical image pixel patterns within the encryption block are encrypted in such a manner that they yield identical cipher blocks, the original image bleeds through.
Clearly, identical blocks of data should not be encrypted in a manner that yields the same cipher text. As a result, the ECB block cipher mode is considered weak security and is not recommended for use.
 |
 |
 |
|
Original Image |
Encrypted using ECB mode |
Encrypted using other mode |
|
Figure 2 |
||
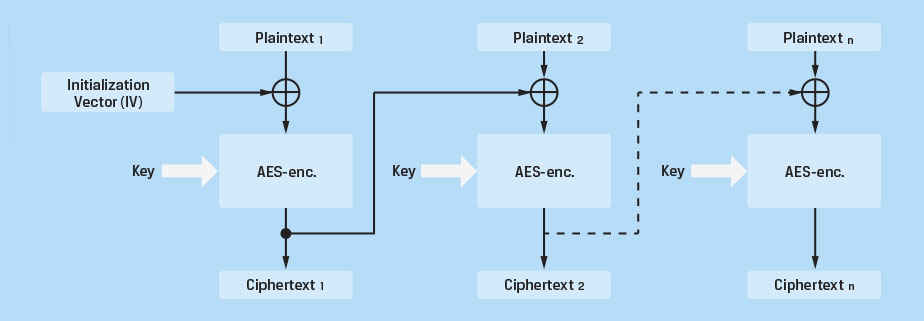
Cipher Block Chaining (CBC). As discussed, the primary weakness with ECB is a result of identical data blocks being encrypted in a manner that produces identical cipher text. The goal is to achieve an encryption method that encrypts each block using the same encryption key, while resulting in different cipher text, even when the plain text for 2 or more blocks is identical. Cipher Block Chaining was designed to achieve this result. Figure 3 is a depiction of CBC cipher mode.
An initialization vector (IV) of 128 bits is generated and combined with the plain text of the first block in a sector. This data is combined using the Exclusive OR (XOR) function. The resulting 128 bits of data are then encrypted using the AES encryption algorithm and stored in the media. The resulting cipher text is passed on to the next block where it is combined with the plain text for that block, encrypted and stored. This process of chaining is repeated for each block in the sector. The process ensures that blocks of identical data result in completely different cipher text. As a result, CBC is much more secure than ECB and is considered to be suitable for most security applications. CBC is widely used in many encrypted Flash drives.
 |
|
Electronic Code Book (ECB) |
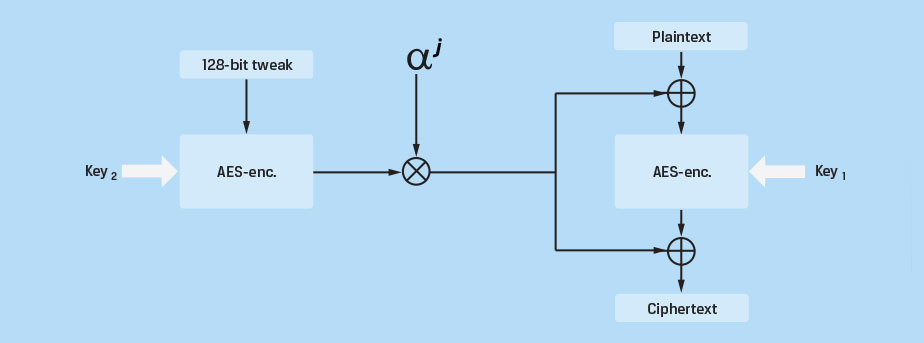
AES-XTS Block Cipher Mode. Originally specified as IEEE Std 1619-2007, NIST added XTS to the list of AES block cipher modes in 2010. XTS is the newest block cipher mode and is the cipher mode used by IronKey drives. It was designed as a stronger alternative to other available block cipher modes such as CBC. It eliminates potential vulnerabilities associated with some of the more sophisticated side channel attacks that could be used to exploit weaknesses within other modes. Figure 4 is a simplified block diagram for XTS mode.
XTS uses two AES keys. One key is used to perform the AES block encryption; the other is used to encrypt what is known as a "Tweak Value." This encrypted tweak is further modified with a Galois polynomial function (GF) and XOR with both the plain text and the cipher text of each block. The GF function provides further diffusion and ensures that blocks of identical data will not produce identical cipher text. This achieves the goal of each block producing unique cipher text given identical plain text without the use of initialization vectors and chaining. In effect, the text is almost (but not quite) double-encrypted using two independent keys. Decryption of the data is accomplished by reversing this process. Since each block is independent and there is no chaining, if the stored cipher data is damaged and becomes corrupted, only the data for that particular block will be unrecoverable. With the chaining modes, these errors can propagate to other blocks when decrypted.
 |
|
Figure 4 |
Conclusion
AES-XTS provides Kingston IronKey hardware-encrypted drives with greater data security than other offerings on the market. All security functions are contained within the confines of the on-board security processor, providing high-grade security and portability.
Additionally, these devices enforce complex password protection and lock down after a specified number of invalid password attempts and will finally crypto-erase the drive’s data. Packaged in a rugged waterproof casing, these devices provide the ultimate security and protection for data. For customers requiring the ultimate level of data protection, select IronKey drives feature the newest FIPS 140-3 Level 3 certification, which provides military-grade security for the highest value data. IronKey enterprise- and military-grade encrypted drives come with three- to five-year warranty and free technical support.